The DevOps Guide to Database Security: Seven Essential Practices
WordPress and Drupal are fantastic content management systems because of their versatility and strength. Both platforms are widely used, storing a lot of sensitive data. Unfortunately, this makes them prime targets for cyberattacks. That’s why securing the database is necessary to protect against unauthorized access, SQL injection attacks and data breaches.
Image

DevOps practices are a reliable solution to enhance database security for your WordPress and Drupal sites. Essentially, it’s a set of practices that combines software development (Dev) and IT operations (Ops). By integrating development, testing and deployment processes, DevOps ensures a smooth workflow that boosts productivity and fortifies security.
A major component of DevOps is that it treats security as code, meaning security policies and configurations are version-controlled, tested and deployed alongside the application code. This helps maintain consistent security across environments. It also consistently checks updates for vulnerabilities before going live, reducing the risk of human error and maintaining security.
If you’re an IT professional, this guide is essential reading. We'll discuss seven essential practices that will help you build a robust database security strategy within your DevOps framework, keeping your data safe and giving you peace of mind 24/7.
Database Security Threats
Software Vulnerabilities
Software vulnerabilities are bugs, flaws or weaknesses in database software that attackers can exploit to gain unauthorized access or cause damage. These vulnerabilities can exist in the software code or arise from misconfigurations, outdated software, or the lack of patches and updates.
One of the most notorious examples is the Equifax breach in 2017. In this breach, attackers exploited an unpatched software vulnerability in the Apache Struts web application framework, exposing the personal information of approximately 147 million people.
Quick Mitigation Strategies
- Regularly update and patch database software.
- Conduct vulnerability assessments and penetration testing.
- Implement automated security tools for continuous monitoring.
Injection Attacks
Injection attacks, mainly SQL injection, happen when attackers manipulate database queries to gain unauthorized access or alter data. They achieve this by manipulating inputs or tampering with parameters.
For instance, in the ResumeLooters attack, cybercriminals used SQL injection to gain access to resumes and personal data stored on several online job portal databases. This resulted in significant negative effects, including personal information theft, privacy violations and damage to the job portals’ reputation.
Quick Mitigation Strategies
- Use prepared statements and parameterized queries.
- Implement input validation and sanitization.
- Employ web application firewalls.
Malware
Malware includes viruses, worms, ransomware and spyware that can infect databases and cause data theft, corruption or unavailability.
Change Healthcare, a healthcare technology company, suffered a malware attack in February 2024 that disrupted its services and compromised sensitive data, including patient records. To prevent the stolen data from being leaked, a $22 million ransom was paid.
Quick Mitigation Strategies
- Regularly update antivirus and anti-malware software.
- Implement email filtering and web security gateways.
- Create regular backups and have a disaster recovery plan in place.
Denial of Service (DoS)
DoS attacks occur when attackers flood a database with excessive requests, disrupting service and making the database unavailable to legitimate users. Common techniques include volumetric attacks and application-layer attacks.
For example, Swiss websites experienced significant disruption during the World Economic Forum due to coordinated DoS attacks. These attacks overwhelmed the targeted websites with excessive traffic, rendering them inaccessible to legitimate users.
Quick Mitigation Strategies
- Implement rate limiting and traffic filtering.
- Employ DoS protection services.
Human Error
Human error, such as misconfigurations, weak passwords and accidental data deletion, can significantly compromise database security. Here are a few common scenarios:
- Misconfigurations due to a lack of knowledge or oversight.
- Use of weak or reused passwords.
- Accidental deletion of critical data.
The Verizon 2024 Data Breach Investigations Report found that 68% of breaches involved a human element. A notable case was the Pegasus Airline incident, where 23 million files, some with sensitive data, were accidentally exposed due to human error.
Quick Mitigation Strategies
- Implement strong password policies and multi-factor authentication.
- Train your employees regularly and provide them with awareness programs.
- Deploy automated tools to manage configurations and monitor for anomalies.
Insider Threats
Insider threats involve employees or contractors intentionally misusing their access to compromise database security, often motivated by financial gain, espionage or personal grievances.
The Tesla data breach is a prime example. Two former employees leaked thousands of personal records to a German news outlet.
Quick Mitigation strategies
- Implement role-based access control (RBAC) and the principle of least privilege.
- Conduct regular audits and monitor user activity.
- Establish a strong insider threat program and response plan.
Understanding the TTPs cybersecurity professionals observe in database attacks helps teams stay ahead of threats. When cybersecurity experts analyze these Tactics, Techniques, and Procedures, they can better predict and prevent future attacks on WordPress and Drupal databases. This intelligence-driven approach complements DevOps practices by integrating security awareness throughout the development lifecycle.
Pantheon’s Top Seven Security Solutions for DevOps Pipelines
As organizations strive to meet these demands, integrating strong security measures within DevOps pipelines has become a critical priority. Let’s take a look at how Pantheon tackles the challenges faced by DevOps teams navigating WordPress and Drupal database security:
#1: Managing Data Residency and Compliance
Imagine getting an email from a CISO (Chief Information Security Officer) asking if the site’s data is stored in the right country. You’ll need to be on top of that, especially if the site operates globally or in regulated industries.
Many countries and regions have enforced strict data protection laws, such as GDPR in Europe and CCPA in California. These regulations often have specific requirements about where data can be stored and processed.
Unfortunately, there's often tension between the DevOps goal of rapid delivery and the need to ensure compliance, which can slow down processes. But, at Pantheon, we make it easy for organizations to manage data storage locations and comply with relevant data residency requirements.
Image

Pantheon provides multiple global regions for hosting websites, including the United States, Australia, Canada and the European Union. This allows organizations to choose where their data is stored to comply with specific data residency requirements. Additionally, Pantheon complies with various data protection regulations, including GDPR, and provides features to help customers meet their compliance obligations, which can help address the CISO’s concerns about data storage locations.
The site’s region can be easily checked through the Pantheon dashboard or using Terminus commands.
Even better, we offer a Client Data Processing Agreement that outlines our data handling practices and commitments to data protection. We also implement robust security practices, including SOC 2 Type 2 compliance. This can ensure the adequacy of organizations’ information security systems.
#2: Preventing Hacker Attacks
Several major security breaches have already occurred due to compromised DevOps pipelines. For example, an attack on Codecov exfiltrated secrets from thousands of build pipelines. This indicates that DevOps pipelines are increasingly becoming targets for hackers because they provide access to sensitive information, intellectual property, and the ability to inject malicious code into software that will be distributed to many users.
Here are some common attack vectors:
- Code injection: Attackers attempt to insert malicious code into applications.
- Unauthorized access: Hackers try to gain unauthorized entry to systems and pipelines.
- Dependency confusion: Attackers exploit the way external dependencies are fetched to run malicious code.
- Poisoned Pipeline Execution (PPE): This technique allows attackers to manipulate the build process by injecting malicious code into pipeline configurations.
Hacker attacks aren’t a pressing problem for teams using Pantheon. Pantheon provides a secure, containerized infrastructure with built-in security features like DDoS protection, intrusion prevention, and a web application firewall (WAF) to protect against common attack vectors.
Pantheon's Secure Integration feature allows for encrypted connections to internal data sources behind firewalls. We also provide managed HTTPS certificates and enforce secure connections between environments. All your websites will have high-grade encryption (TLS 1.3) and will be deployed worldwide with Pantheon’s Global CDN.
Last but certainly not least, Pantheon offers granular user access controls and role-based permissions to limit potential attack surfaces. Our SAML integration enables additional security features such as multi-factor authentication and single sign-on (SSO). This also allows customers to enforce minimum password strengths and authentication audit logs.
#3: Mitigating Vulnerabilities in Pipeline Tools/Dependencies
Many DevOps pipelines rely heavily on open-source tools and libraries. These dependencies can contain publicly disclosed vulnerabilities that make the pipeline vulnerable to attack if left unpatched. Exploiting known vulnerabilities in outdated or unpatched pipeline components is a low-hanging fruit for attackers. They can exploit these weak points to gain unauthorized access to source code, build systems, artifact repositories, etc.
Image

To tackle this problem, Pantheon automatically applies security patches and updates to the underlying platform, reducing the risk of vulnerabilities. With its Dev, Test, Live workflow and Multidev environments, teams can securely code and test before deploying to production.
Additionally, Pantheon provides Integrated Composer functionality for both Drupal and WordPress sites. This enables one-click updates from the dashboard for Upstream updates and Composer dependencies on Composer-managed sites.
#4: Eliminating Data Loss and Enabling Quick Recovery
DevOps environments are highly dynamic with tightly connected components. Human error, software/hardware failures, cloud outages, ransomware attacks or disasters can all lead to data loss. With proper backups, companies can retain valuable source code, configurations and project data. These data loss incidents can cause missed opportunities and financial losses.
Regular, automated backups allow you to quickly restore data and get systems back online if an incident occurs, minimizing downtime and disruption to development workflows. Without backups, recovery could take weeks or could even be impossible.
Luckily, Pantheon's automatic backups provide a convenient, reliable and customizable way to protect your site's data at the infrastructure level.
Image
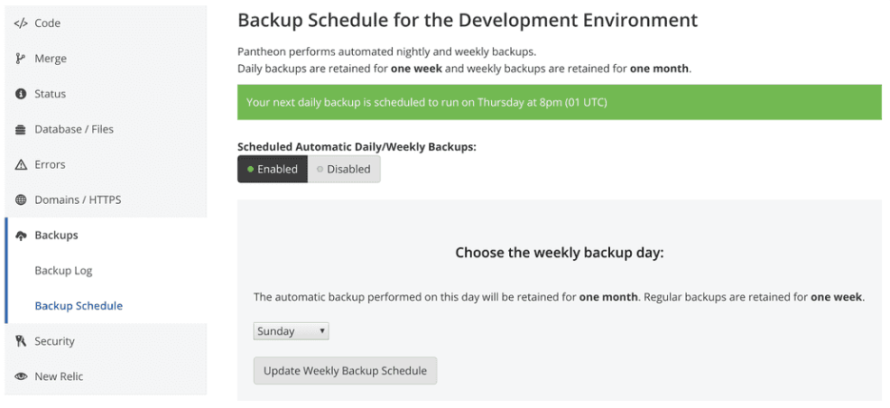
Pantheon allows you to enable automatic daily and weekly backups.
Daily backups are kept for seven days, while weekly backups are kept for about a month (32 days by default). The weekly backup retention period can be customized using the --keep-for option when enabling automatic backups.
The backups are stored offsite on Google Cloud Storage for redundancy and reliability and no file size limitations exist. These automatic backups include separate archives for the site's code, database and files. You can use any automatic backup to restore the environment directly from the Pantheon Dashboard. The restoration process will overwrite the environment's current code, database, and files with the backed-up versions.
The Backup Log in the Pantheon Site Dashboard shows the status of in-progress backups. Long-running backups may indicate a need to optimize the site.
Image
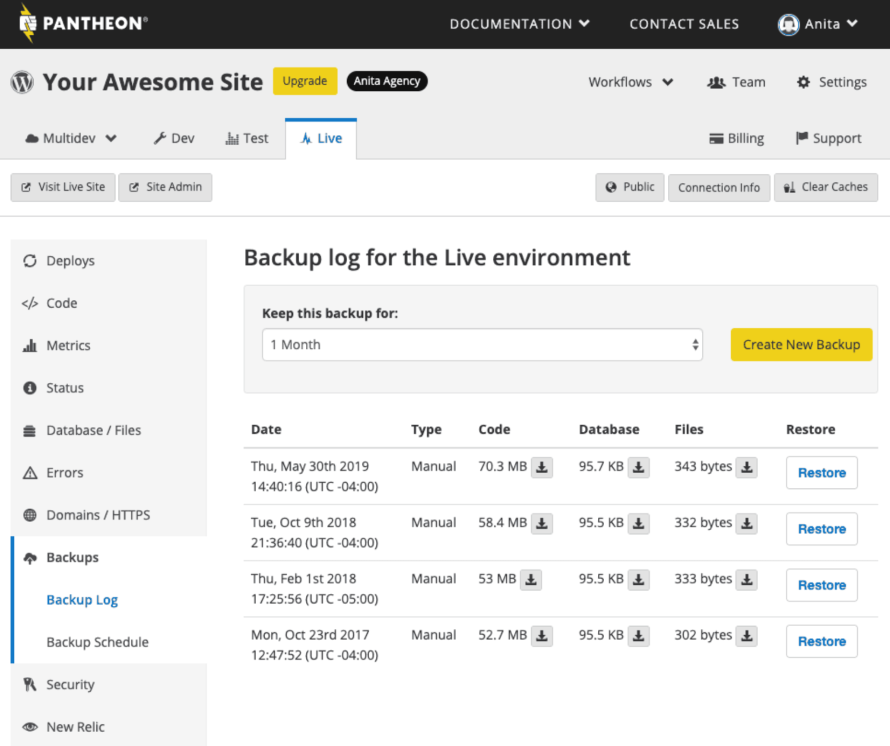
Expert Tips:
- The backup:automatic:enable Terminus command enables automatic backups. It optionally specifies the day of the week for weekly backups and the retention period in days.
- The backup:automatic:info command displays the current automatic backup schedule.
#5: Reducing the Risk of Vulnerabilities Reaching Production
Pantheon's New Relic integration provides real-time visibility into application performance, allowing developers to identify and resolve issues quickly. New Relic's proactive anomaly detection uses machine learning (ML) to identify emerging issues early, minimizing downtime and ensuring system stability.
Image
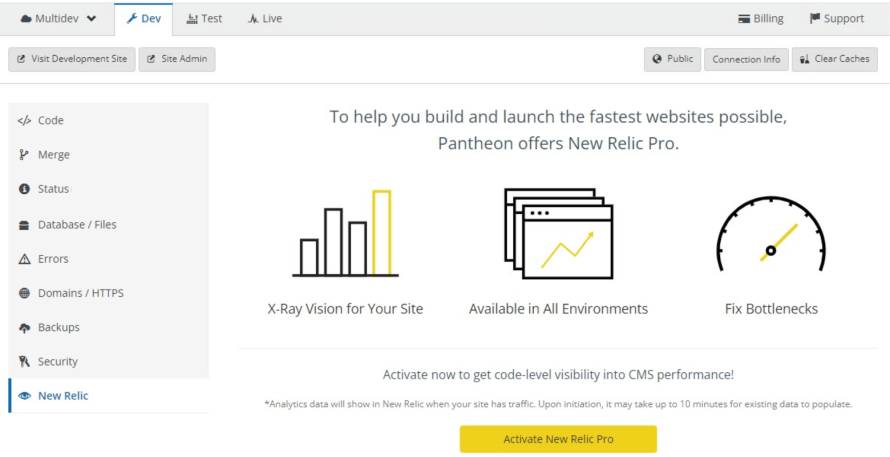
Pantheon's New Relic integration.
This feature helped Clarivate's team to optimize and fine-tune its site-wide performance. It alerted them that a WordPress plugin was making excessive database calls, affecting performance. Based on that, they switched strategies and improved their site significantly.
Additionally, New Relic's full-stack observability gives developers insights into application, infrastructure, and service performance metrics to optimize the system effectively. Distributed tracing and service maps help quickly diagnose issues across microservices.
#6 Keeping Software Up-to-Date All the Time
Outdated CMS versions, plugins, modules and themes pose significant security risks. Vulnerabilities in these components are common attack vectors. That’s why we highly recommend minimizing plugins/modules and regularly updating the CMS and all components to maintain website security.
The Autopilot feature automatically detects and deploys updates for WordPress and Drupal CMS solutions to make things easier for Pantheon users. This keeps sites secure without manual intervention. Key capabilities include:
- Automatic monitoring of portfolios of sites and detecting when updates are available.
- Performing updates in an isolated Multidev environment while maintaining each site's critical dependencies.
- Visual regression testing (VRT) alerts users when an update affects a site's layout/look.
#7 Mitigating Total Datacenter Failure
A complete data center outage, whether from a natural disaster or significant system failure, can bring down a company's website, leading to costly downtime, data loss and damaged reputation. Minutes or hours of downtime can have a severe business impact.
To mitigate this risk, we have engineered a high-availability Multizone Failover solution that provides:
- Real-time replica: While a site is live in its primary data center, a real-time replica is kept online in a secondary availability zone.
- Intelligent failover: Pantheon automatically reroutes traffic to the replica via our Global CDN layer in partnership with Fastly, if the primary data center fails. This enables near-instant failover without manual DNS changes.
- Persistent Coverage: Pantheon immediately provisions a new replica in a third healthy data center after failing over to the secondary zone to maintain redundancy.
- 99.99% Uptime SLA: Multizone Failover comes with a 99.99% uptime guarantee and 24/7 real-time support to actively respond to any incident.
This multizone active/passive architecture ensures high availability and disaster recovery for mission-critical sites. The recovery point objective (acceptable data loss) is 5 minutes, and the recovery time objective (time to restore service) is 15 minutes.
With Pantheon's Multizone Failover, DevOps and security teams can deliver highly available, resilient sites without architecting and managing their own complex disaster recovery systems.
Additional Best Practices for Securing Your Data
Access Control and Authentication
To keep your database secure, it's crucial to use robust access control and authentication. Here are some essential practices:
- Role-Based Access Control (RBAC): Use the principle of least privilege to define roles and assign permissions. Ensure users only have the access necessary to perform their jobs. Limiting access minimizes the probable damage that can arise if an account is breached.
- Multi-Factor Authentication (MFA): Implement MFA to add an extra layer of security. This decreases the risk of unauthorized access even if credentials are compromised. MFA typically combines the user password with a mobile device or security token.
- Regular audits: Conduct regular audits of user access and permissions. Revoke access for users without it and ensure compliance with security policies. Audits help identify any discrepancies or inappropriate access, maintaining a secure environment.
- Automated access management tools: Automated access management tools can reduce the risk of human error and ensure consistent application of access policies. They can streamline the process of granting, modifying, and revoking access, ensuring that adhering to security policies is consistent.
Data Validation and Quality Monitoring
Ensuring the integrity and quality of data is essential to prevent security breaches. Key practices include:
- Input validation: Implement strict input validation to prevent injection attacks. Ensure that all data entering the system is sanitized and validated. This helps prevent malicious data from corrupting the database or executing unintended commands.
- Data quality monitoring: Automated tools are used to monitor data quality continuously. They identify and rectify inconsistencies, anomalies and errors in the data. Maintaining high data quality ensures that the database remains reliable and secure.
- Regular data audits: Conduct regular audits to verify the accuracy and integrity of the data. This helps identify potential security issues early. Regular audits can also uncover errors or malicious changes that may otherwise go unnoticed.
- Compliance with standards: Ensure data validation and quality monitoring practices comply with relevant industry standards and regulations (e.g., GDPR, HIPAA). Compliance enhances security and ensures that your organization avoids legal penalties.
Disaster Recovery Planning
A strong disaster recovery plan can ensure data availability and integrity in a security incident. The main components include:
- Regular backups: Make regular backups and store them securely. Implement automated backup solutions to decrease the risk of data loss. Regular backups ensure you can salvage your data quickly in case of a violation or other disaster.
- Recovery testing: Regularly test the disaster recovery plan to ensure that data can be restored swiftly and accurately if an incident occurs. Testing validates the plan's effectiveness and helps identify areas for improvement.
- Redundancy and failover: Implement redundancy and failover mechanisms to ensure continuous data availability. This includes using geographically dispersed data centers. Redundancy ensures that if one data center fails, others can take over, minimizing downtime.
- Documentation and Training: Maintain comprehensive documentation of the disaster recovery plan and train relevant personnel on its execution so they can respond quickly and effectively if an incident occurs.
Employee Security Awareness Training
Human error is a huge element in many security breaches. Effective employee security awareness training can mitigate this risk. Key practices include:
- Regular training sessions: All employees should receive regular security awareness training sessions. These sessions should cover topics such as phishing, social engineering and secure password practices. Regular training emphasizes security for employees and reinforces best practices.
- Simulated attacks: Use simulated phishing attacks and other exercises to test employee awareness and response to security threats. Simulations help employees recognize and respond more effectively to real threats.
- Policy communication: Ensure that employees are aware of and understand the organization’s security policies and procedures. Clear communication helps ensure that everyone has clear expectations and knows how to adhere to security protocols.
- Continuous learning: Provide constant learning opportunities and updates on the most recent security best practices and vulnerabilities. Security is constantly evolving, and ongoing education helps employees stay informed about new risks and defenses.
Roadmap to Database Security in DevOps
With many potential threats, ranging from software vulnerabilities and injection attacks to malware, DoS attacks, human error and insider threats, it’s clear that database security is a critical concern for WordPress and Drupal sites. These threats can have extreme consequences if not addressed properly, making DevOps teams have to prioritize security in their workflows.
One of the most effective ways to secure your database is to choose a hosting provider with built-in security standards. Pantheon is the fastest hosting platform for WordPress and Drupal sites.
Our WebOps infrastructure provides enhanced security through automated updates, guaranteeing that your software is always up-to-date with the latest patches. The Advanced Global CDN with WAF adds another layer of protection against common attack vectors, while New Relic’s continuous monitoring helps detect and respond to potential threats in real time.
Watch our demo to discover how Pantheon can simplify your DevOps workflows and provide peace of mind with top-notch security!