The Pantheon Blog
Brandfolder Image
Latest insights
Why we’re deploying a new PHP runtime
Read MorePantheon Joins Drupal AI Initiative
Read MoreFrom ChatGPT to AI Overviews: How Enterprises Win in Multiplatform AI Search
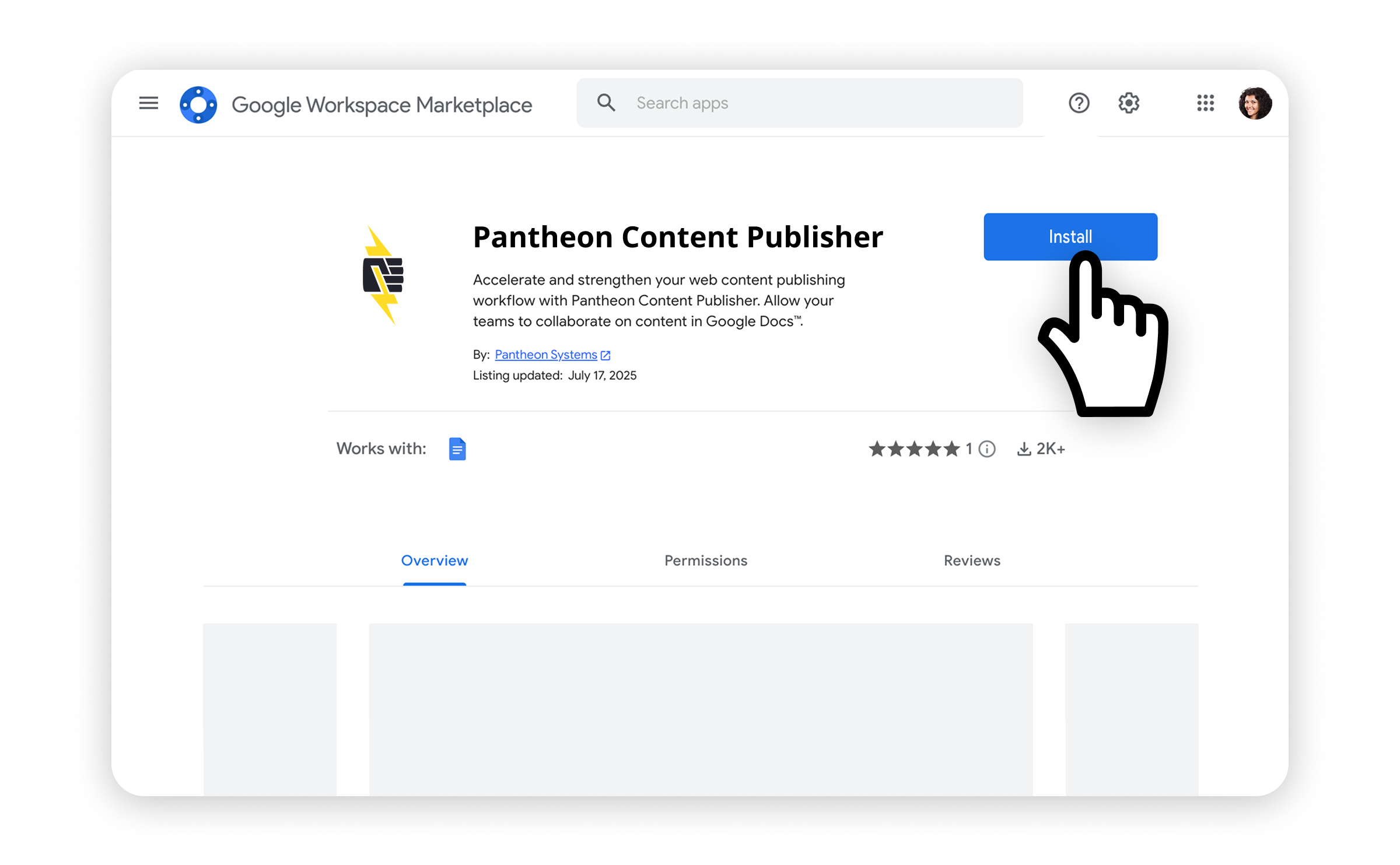
Read MoreWhy Anderson Cooper Should Use Content Publisher
Read MoreWhere do you really manage your content?
Read MoreNew in Content Publisher: Smarter Styling, Layouts and WordPress Plugin
Read MoreTop Four Upgrades to Pantheon’s Support Experience
Read MoreNavigating the Noise: A Look at Bot Traffic on Pantheon
Read MoreAll's FAIR: Why WordPress needs decentralization
Read MorePantheon protects you from the latest WordPress security exploits
Read MoreModernizing Pantheon's Site Dashboard
Read MoreIntroducing Pantheon’s Trust Center: Transparency Meets Performance
Read More