Conor Bauer , Product Manager Reading estimate: 9 minutes
Halting DDoS Attacks: Effective Strategies for Prevention
In a DDoS attack, a website faces a surge in traffic beyond its capacity. Botnets, networks of infected devices controlled remotely by hackers, play a central role by simultaneously generating a massive volume of traffic from various sources. Upon the attacker's command, these botnets flood the target website or server with requests, causing it to crash under the excessive load.
For businesses, being hit by a Distributed Denial of Service (DDoS) attack can mean losing customers' trust and a lot of money. For example, a significant DDoS campaign in 2023 targeted the US healthcare sector, led by the hacktivist group KillNet.
The Health Sector Cybersecurity Coordination Center (HC3) and the Cybersecurity and Infrastructure Security Agency (CISA) reported that KillNet, a pro-Russian group active since at least January 2022, focused its attacks on healthcare organizations supporting Ukraine. The healthcare sector was warned to remain vigilant and implement protective measures against such cyber threats.
Faced with such threats, effective strategies are needed to safeguard your online business from DDoS attacks. In this article, we’ll teach you how to keep your platform secure and accessible to users.
The Types of DDoS Attacks: Volumetric, Protocol and Application Layer Attacks
Understanding the nuances of DDoS attacks is important. Each unique type of DDoS attack comes with its own potential damages and the disruptive effects they can inflict on websites and networks. There are three main types to look out for:
Volumetric Attacks
Image
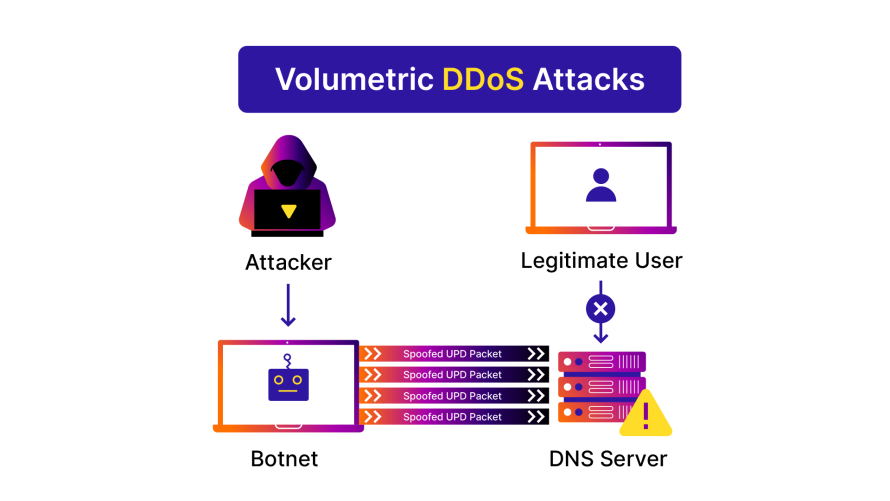
Volumetric attacks aim to incapacitate a network's infrastructure by inundating it with exceptionally high volumes of data. Executed by flooding the target with overwhelming traffic, these attacks saturate bandwidth, leading to service inaccessibility. The potential damage is substantial, causing network downtime, operational disruptions and financial losses.
Protocol Attacks
Image
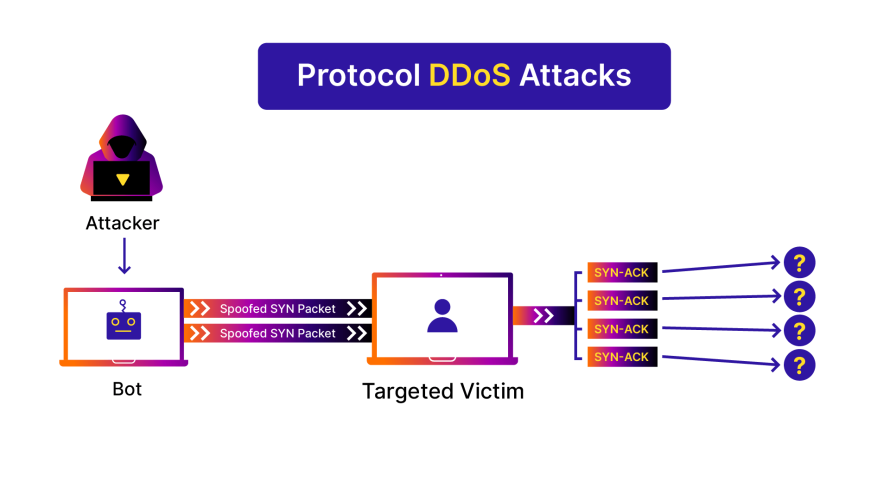
Protocol attacks exploit vulnerabilities in server resources and network layers. By targeting weaknesses in communication protocols, these attacks exhaust server resources, hindering overall functionality. The resulting damage can manifest as disruptions in essential services, potential server crashes and compromised network stability.
Application Layer Attacks
Image
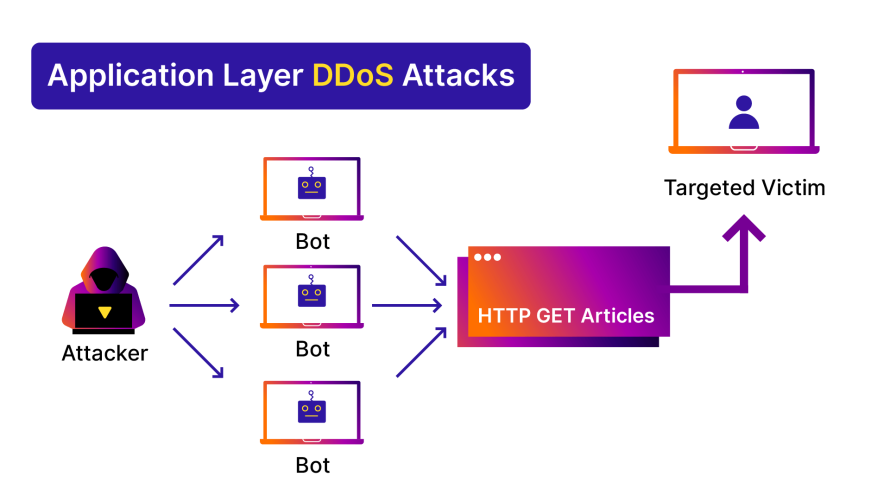
Application layer attacks employ a different strategy, disguising themselves within legitimate-looking traffic while focusing on the application layer. Executed by overwhelming specific application resources, these attacks hinder user access and cause service degradation. The consequential damage includes impaired user experience, potential loss of sensitive data, and compromised application functionality.
Four Strategies to Prevent DDoS Attacks
While the threat of DDoS attacks can seem daunting, there are effective strategies and tools to guard against these digital onslaughts:
Attack Surface Reduction
One of the first steps in defending against DDoS attacks is to minimize the number of vulnerabilities attackers can exploit. This means keeping your systems up-to-date with the latest security patches and updates.
This involves hardening your systems (making them tougher targets), closing unnecessary ports and restricting access only to those who really need it. You want to make it difficult for the attackers to find a way in.
Real-Time Threat Monitoring
Real-time threat monitoring is crucial for detecting and responding to DDoS attacks as they happen. It involves looking for and identifying suspicious patterns that could indicate an attack is underway.
The faster you can detect a DDoS attack, the quicker you can respond, minimizing potential damage. This requires a dedicated team or an automated system that's always on guard.
Using a Content Delivery Network (CDN)
CDNs are networks of distributed servers that are located across the globe. While it's true that they can offload traffic by serving cached versions of your web pages (such as images, videos and other static resources), this is only one piece of the puzzle.
The essence of CDN-based DDoS mitigation is:
- Edge Security: By analyzing and deciding on the legitimacy of web traffic close to the user (at the edge) and away from the core infrastructure, CDNs can effectively block malicious traffic and neutralize threats before they reach and impact the primary hosting resources.
- Bypassing Attack Traffic: In the event of an attack, CDNs can reroute legitimate traffic away from the attacked paths, ensuring uninterrupted service for users. This capability, often referred to as "traffic shaping" or "load balancing”, helps maintain availability even under duress.
- Anonymity of the Origin Server: By using a CDN, the actual IP address of the origin server can be hidden from the public. This makes it more difficult for attackers to directly target the origin server since they must go through the CDN, which has mechanisms in place to protect against attacks.
Rate Limiting and Request Throttling
Rate limiting and request throttling are crucial for controlling incoming traffic by setting limits on the number of requests a user or IP address can make within a specific timeframe. This prevents overwhelming the server with excessive requests, which could lead to a denial of service.
For example, allowing up to 100 requests per minute per user and blocking or slowing down additional requests beyond this limit. These measures not only effectively manage server load but also help identify malicious activity trying to overload the system by triggering rate limits with a large number of requests.
How the Combination of Web Application Firewalls (WAF) and DDoS Protection Work
In DDoS attack prevention, Web Application Firewalls (WAFs) and DDoS protection are important. WAFs possess a foundational architecture that inspects incoming traffic, identifying and blocking malicious requests to inherently safeguard against DDoS attacks. On the other hand, DDoS protection systems are great at distinguishing between genuine high traffic and a DDoS attack by employing advanced algorithms that analyze patterns and behaviors.
The synergy of WAFs and DDoS protection offers coverage against a broad spectrum of DDoS attack types. This combination enhances overall security, as WAFs act as proactive barriers, and DDoS protection systems dynamically respond to potential threats. Simultaneously, DDoS protection absorbs and scatters incoming traffic to prevent overload, while WAFs focus on inspecting requests with precision, reinforcing security layers.
Unlike traditional firewalls that monitor traffic between servers, WAFs are designed to protect specific web applications. They scrutinize incoming traffic to your web applications and make decisions about what to let through and what to block.
DDoS protection systems are the heavy lifters in terms of managing and mitigating large volumes of traffic designed to overwhelm. They are specialized solutions that detect and protect against DDoS attacks, distinguishing between legitimate high-traffic volumes (like a spike in website visitors) and malicious DDoS attempts.
When WAFs and DDoS protection systems work together, they provide comprehensive coverage against a wide array of DDoS attack types, ensuring that both the volume and the nature of incoming traffic are meticulously managed.
While the DDoS protection system absorbs and diffuses the massive traffic volumes characteristic of DDoS attacks, the WAF focuses on inspecting the content of individual requests.
An excellent example of this combination in action is our approach to cybersecurity. At Pantheon, we use smart monitoring to identify potential issues promptly.
We use distinct mitigations within the Global CDN that apply to all sites, customer-specific Advanced Global CDN implementations, and our load balancing layer within Google Cloud. This structure facilitates quick updates and adjustments across the entire network, enhancing the effectiveness of both WAFs and DDoS protection.
Cloud-Based Protection and Behavioral Analysis in Halting DDoS Attacks
Cloud-based DDoS protection offers a dynamic shield against attacks. This approach has several benefits:
- Scalability of Resources: During an attack, the cloud can provide additional bandwidth and processing power to absorb and mitigate the influx of malicious traffic.
- Edge Density: Cloud services often have a global network of data centers, which means there's likely to be a server near any given user or attacker. This proximity allows for the rapid filtering and blocking of malicious traffic before it can reach and impact the target. For Pantheon customers, this means a separation between the CDN points of presence runs through Fastly and the origin infrastructure runs in Google Cloud.
- Traffic Distribution: By distributing traffic across a worldwide network, cloud-based systems can effectively dilute the impact of volumetric DDoS attacks. This means that instead of hitting a single target, the attack traffic is spread out.
Behavioral analysis takes DDoS defense to a new level, scrutinizing traffic patterns to identify unusual behavior that may indicate an attack. Additionally, anomaly detection monitors network traffic to detect deviations from normal patterns, like sudden traffic increases or unusual requests, which can indicate a potential DDoS attack.
When combined, cloud-based protection and behavioral analysis form a comprehensive defense strategy against DDoS attacks.
The Role of Pantheon’s Advanced Global CDN in DDoS Attack Prevention
Image
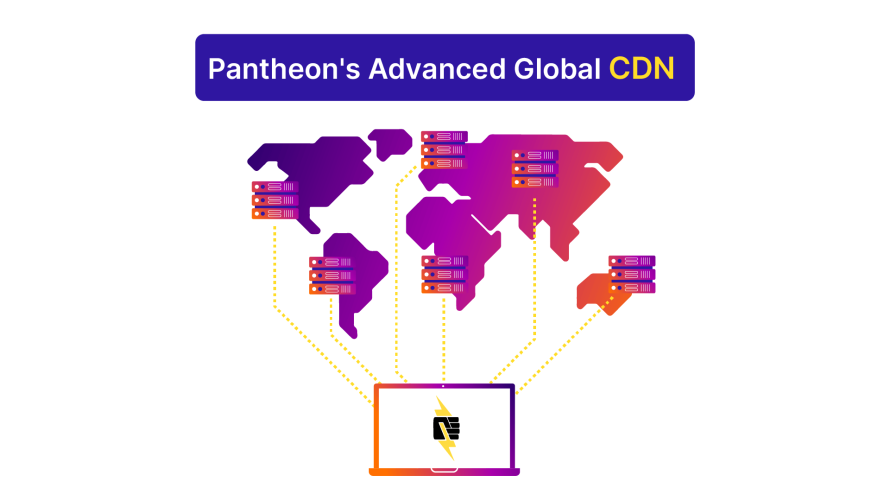
Pantheon's Advanced Global CDN is an additional layer of Fastly configuration specific to each customer who uses it that augments our platform-wide Global CDN. It uses cutting-edge technology and strategic approaches to fortify websites against the barrage of DDoS threats. Here’s how:
- Location-Based Blocking: This allows for the restriction of traffic from specific geographic locations, which is particularly useful if an attack is identified as originating from a certain area.
- Redirection: Traffic can be intelligently redirected to protect the integrity of the website or application.
- IP Blocklisting: Suspicious IP addresses can be blocked from accessing the network, preventing known attackers from launching further attacks.
- Optimal Tuning for CMS and Geolocation: Our platform-wide Global CDN already contains tunings for WordPress and Drupal. With AGCDN, customers can make further CMS-specific and geolocation refinements, ensuring optimal performance and security tailored to specific needs.
We also employ innovative rate limiting techniques like JA3 fingerprinting to distinguish between legitimate users and potential attackers, which enables us to effectively manage heavy traffic without impeding the experience of genuine users.
At Pantheon, our approach to preventing DDoS attacks is multi-faceted:
- Secure Infrastructure: The foundation of our defense strategy is our secure, resilient infrastructure designed to withstand cyber threats.
- Proactive Monitoring: Daily checks and continuous monitoring enable the early detection of potential security issues.
- Strong Compliance: Adherence to stringent security standards ensures the infrastructure remains robust against attacks.
- Isolating Traffic Streams: By isolating traffic, our Pantheon platform can effectively manage and analyze incoming data, identifying threats more accurately.
- Container-Based Cloud Architecture: This setup allows for the safe and isolated deployment of applications, reducing the risk of widespread impact from attacks.
- Additional Resource Allocation During Attacks: In the event of an attack, resources are allocated to ensure that performance remains unaffected.
- Collaboration with Upstream Providers: We work closely with our providers like Fastly and Google Cloud to address and mitigate network-level threats.
Our prevention strategy mitigates the immediate effects of DDoS attacks and contributes to creating a safer online environment for businesses and their users.
How Pantheon Protects Against DDoS Attacks For Each Site at Every Plan Level
Image

Our defense mechanisms and engineering team at Pantheon stand ready to ensure that every client, regardless of their size or plan, remains protected and operational.
During a notable DDoS attack against a specific site, we faced a situation where the PHP worker processes for a specific site were pushed substantially over capacity. This resulted in an unusual spike in 503 response codes, signaling that the container was temporarily unable to handle the request due to being overwhelmed by the attack.
This particular customer was on a basic hosting plan, but that did not affect our response. By identifying the characteristics of the malicious traffic, our operations team was able to deploy a targeted filter designed to block the attack vectors without disrupting legitimate traffic. With this precise intervention, we neutralized the threat efficiently, restoring normal service operations and ensuring the integrity of the client's site.
Take your DDoS Protection to the Next Level With Pantheon
DDoS attacks are a serious threat to business continuity, data security and customer trust.
A robust DDoS response plan rests on four pillars:
- Identification involves detecting an attack in its early stages and leveraging real-time monitoring to spot unusual traffic patterns.
- Classification requires understanding the type of attack, whether it's volumetric, protocol, or application-layer, to apply the most effective countermeasures.
- Tracing the attack back to its source helps in understanding its nature and potentially identifying the attackers.
- Neutralizing the attack involves deploying strategic defenses to mitigate its impact and utilizing tools and techniques tailored to the specific threat.
Having these elements in place ensures that when an attack occurs, your team can move efficiently to minimize its impact, keeping your services running and your users protected.
When you use Pantheon, your online presence is protected, capable of handling traffic surges without a hitch, and consistently reliable.
Additionally, with Pantheon's Advanced Global CDN, you gain access to a comprehensive DDoS response plan that protects against attacks and enhances your website's performance across the globe.
Don’t wait for an attack to test your defenses. Secure your sites by putting them on Pantheon today.
Topics
Discover More
Staying Ahead In The Game of Distributed Denial of Service Attacks
Steve Persch
Reading estimate: 3 minutes
Learn how healthcare sites can thrive with modern development tools
Jason Yarrington
Reading estimate: 3 minutes
Activate Email Domain Authentication To Build A Less Spammy World
Manoj Sarma
Reading estimate: 4 minutes